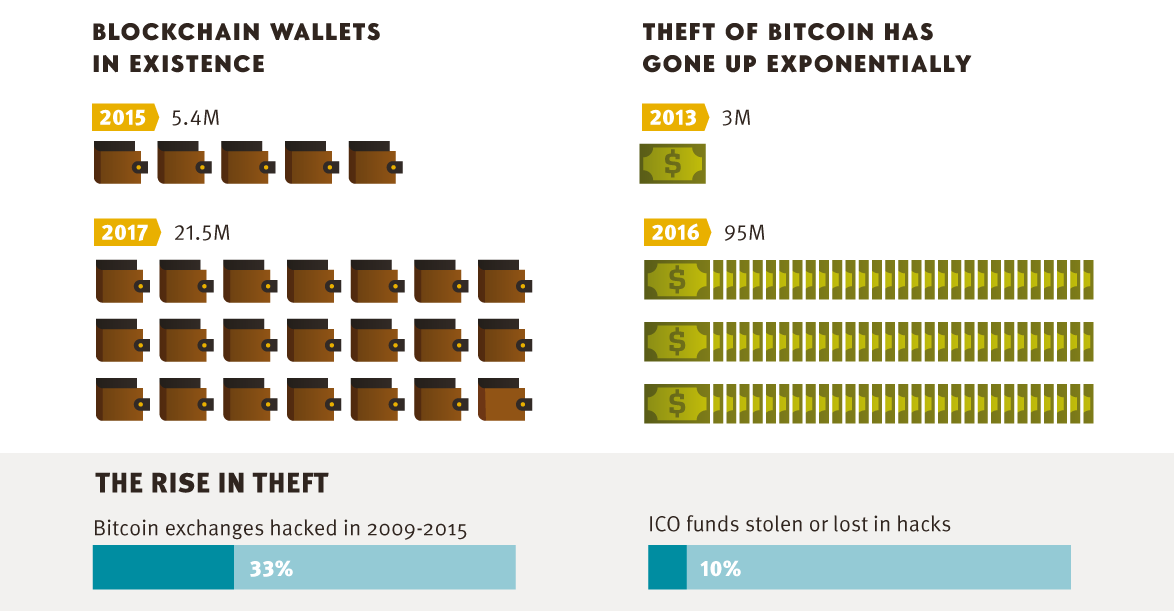
As cryptocurrency continues to rise in prominence, so do instances of crypto theft. Here are the steps to take to avoid being a sucker. Source/More: Infographic: The Problem of Crypto Theft,... Read more
Civil libertarians and security researchers have long been concerned that otherwise inadmissible intelligence from the agency is used to build cases against Americans though a process known... Read more
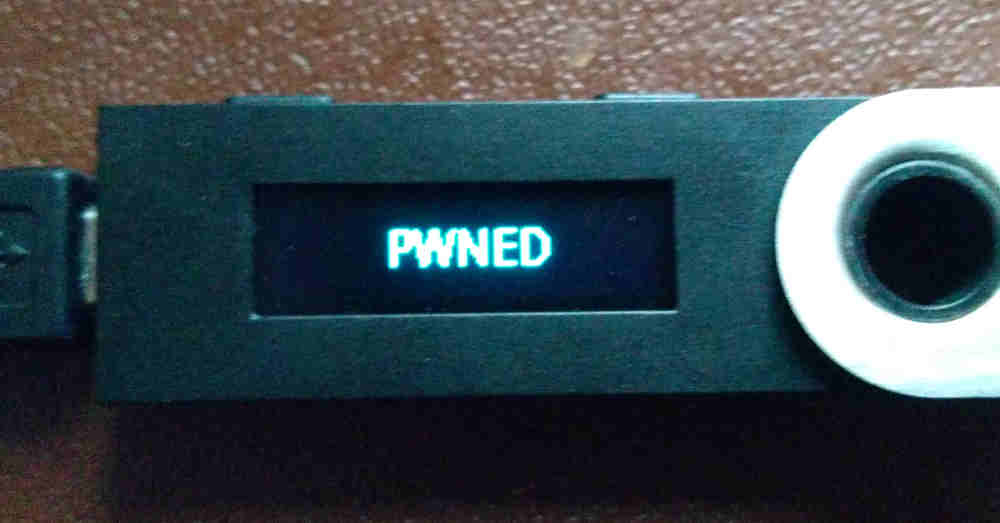
In this post, I’m going to discuss a vulnerability I discovered in Ledger hardware wallets. The vulnerability arose due to Ledger’s use of a custom architecture to work around many of the li... Read more
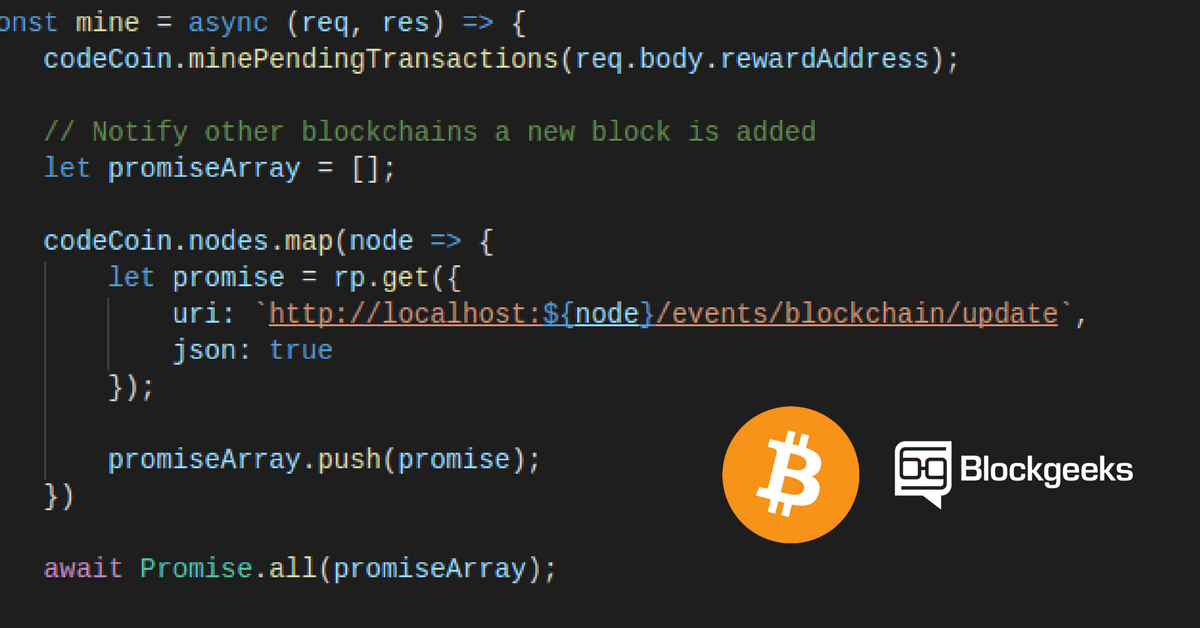
This tutorial will explain you to build a blockchain which returns mining rewards. How To Code a Bitcoin “like” Blockchain In JavaScript As we like simplicity, we will only use t... Read more
Jimmy Song’s Programming Blockchain workshop taught me about a lot more than bitcoin. “All models are wrong, some are useful.” This phrase was coined by the statistician Ge... Read more
Innovative companies are rushing to create real-world business applications that combine artificial intelligence (AI) and blockchain technology. For example, JD.Com, the largest retailer in... Read more
Leaked emails between IOTA developers and researchers have landed the cryptocurrency in hot water. Nerd fights are the the background radiation of the cryptocurrency universe, but occasional... Read more
Ivy-lang, Plutus, Solidity, Scrypto, Michelson, Hoon, Rust, … When should I find the time to explore all these languages? Most of them are barely used, making it incredibly hard to adopt the... Read more
In light of recent rumors of a collaboration between Litecoin and Monero (debunked by coin creators Charlie Lee and Riccardo Spagni), we take a look at the potential repercussions of such a... Read more